Alert 1! Alert 1! Action Message Follows
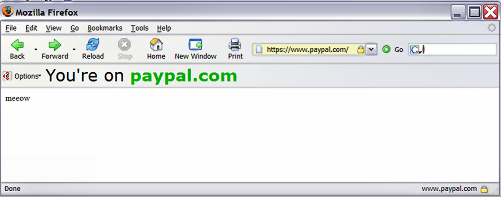
There is a web-based spoof vulnerability that works on Opera 7.54u2 and Firefox 1.0, but not IE 6/SP2. The proof of concept comes from Shmoocon (advisory here and proof web page here). The vulnerability allows anyone to spoof *any* domain, including those with SSL certificates (you know, those with https:// addresses). While viewing the certificate would show the actual, rather than spoofed site, how many people actually view the certificates to check the URL?
The spoof also fools Spoofstick so using that utility will not help you. On SSL sites, too bad it doesn't read the certificate and display the site URL.
There are three workarounds (that I know of). Look at the underlying HTML to see the actual URL. Never click on links (either on web pages or emails). Instead, type the URL yourself into your browser. Or lastly, a poster in the Firefox support forum says to do the following if you are using Firefox:
The workaround for Firefox seems to be an edit to your compreg.dat.
For windows
c:\Documents and Settings\$USER\Application Data\Mozilla\Firefox\Profiles\default.random\compreg.datFor UNIX
~/.mozilla/firefox/default.random/compreg.datRemoving the line that references IDN makes the problem go away. Using Find, there was a single reference for the UNIX host and 2 for the Win32 host [I found only one in mine -ed]. Removing the lines and restarting the browser makes the attack fail regardless of the about:config/userprefs.js value.
Here's an example entry.
{4byteshex-2byteshex-2byteshex-2byteshex-6byteshex},@mozilla.org/network/idn-service;1,,nsIDNService,rel:libnecko.so
Cheers,
-BeesTQuote:
It works. After making a backup of compreg.dat i placed#
to remark out the line BeesTea See Profile mentioned. Exploit fails
Quote:
Confirmed on Linux, also.
I can confirm that implementing the above (and clearing your cache and then shutting down and restarting Firefox) will keep the browser from going to the spoofed URL but all you get is an error message saying the paypal.com site cannot be found. I guess that's better than nothing but it's hardly informative unless you remember this is telling you a site may be spoofed.
UPDATE: You also need to type in "about:config" in Firefox and find the reference to IDN (use the filter to find the instance of idn). Once found, change the default from "true" to false" (just double click on the line to bring up the choice).
Over at the Opera Forum on this problem, Opera is essentially saying it's not their problem to fix and even if they did, the solution would keep people from using, for example, Greek or Russian sites (sounds good to me - ed.).
I dunno what I'm going to do about Opera. I understand their point-of-view. But. If companies have learned nothing from Microsoft's stumbling examples, then learn this: IT'S THE SECURITY, STUPID.